By Erik Kleinsmith, Associate Vice President, Intelligence Studies, National Security & Homeland Security
Editor’s Note: This is the first article in a two-part series investigating censorship.
Information warfare, like intelligence operations, use to exist primarily within the realm of military and national security. As members of what could be considered the U.S. Army’s first generation of information warriors, it was our job to combine the disciplines of deception, psychological operations (PSYOP), operational security (OPSEC), cyber warfare, among other aspects into coherent strategies to gain and maintain dominance over our enemies in the information spectrum.
Efforts to collect this information included using both open and classified methods to promote and protect our access to the information while at the same time denying, degrading, and disrupting our enemies’ access to that information.
As recent years, months, and especially the past few weeks have revealed, it is now evident that information warfare has slipped beyond the purview of national interest and security, and is now an inextricable part of our society.
No longer satisfied with arguing or spinning a story for one side or against the other, political operatives, activists, and tech and media companies have recently embraced the more radical tactics of shadow banning, demonetizing, and outright censorship of their competitors, adversaries, and people they just don’t like.
By turning these techniques against their fellow citizens, these self-proclaimed arbiters of truth and justice left unchecked are supplanting due process and many of the freedoms that are demanded in Western democracies.
A Road Map of Censorship
Going well beyond policing illegal or incendiary speech as a form of information warfare, censorship seeks to control a narrative not by arguing or promoting opposing ideas through public discourse, but also by attempting to make it so the opposing idea never reaches the intended recipients in the first place.
For anyone who relies upon data, information, and analysis as the essence of their work (i.e., intelligence, security, law enforcement professionals and even business and academic researchers), understanding this brave new world of censorship and control of information is critical for developing a plan or strategy to operate successfully in this new environment.
A big part of this understanding lies in placing the most popular methods of censorship within the context of where they are most commonly practiced. To do this, we need a map of today’s model of communication and messaging along with where and how the model can be controlled or severed altogether.
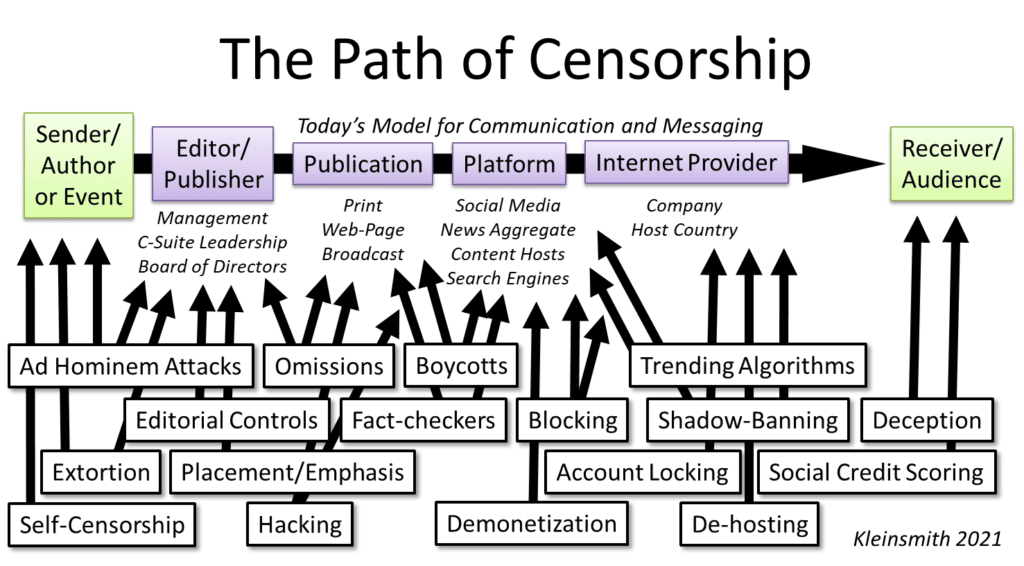
A long-ago departure from the days of receiving the daily newspaper, today’s model for communication and messaging still flows from the sender (i.e., the author or the event) to a receiver or audience, but now the model flows through a series of publishers, platforms and providers along the conduit of the internet.
Following this primary method of getting a message or information to an intended audience, this path presents the information warrior with several opportunities to degrade, disrupt, or deny that message along the way. Many of the most popular, recent, and successful methods are listed below this path along with where they are most efficiently conducted.
External Censorship of Information Warfare
It’s important to note that many of these methods are either internally or externally driven. External censorship in the form of ad hominem attacks, extortion, and boycotts organized against the author, publication or platform come from outside groups that can use character assaults, smears, blackmail, threats, or other demands intended to kill the message by ensuring the messenger never writes or speaks it.
If in a written form, such attacks can ensure that the writing is never published using threats of lawsuits or loss of business. These methods can also take the form of paying fact checkers to discredit stories or statements that go against the attackers’ given narrative. Authors and publishers can also be paid or pressured to promote their own version of events or simply to ignore a story altogether.
Internal Forms of Censorship
What is more difficult to understand are methods of censorship that are internally practiced by those who are responsible for conveying information. Traditional publishers, including news or media companies, or newer forms of media such as independent bloggers or video bloggers can easily inject their own biases by omission or placement of the story so that it is technically covered, but hard to find.
Some of the most prominent examples of late have been censorship by tech platforms that have taken unprecedented steps to suspend, block, label, or ban certain phrases, hashtags, stories, and even people and entire publications they disagree with.
Currently, tech platforms are protected from being held liable for the content others publish or post on their sites under Section 230 of the Communications Decency Act or Title V of the Telecommunications Act of 1996. There is a big debate raging now whether or not tech providers who conduct acts of censorship should be further defined as platforms under U.S. law. The argument here centers around the question of whether tech providers should lose these protections as they’ve have taken a more active role in censoring content that is not expressly illegal.
Understanding Why Censorship is so Dangerous
This map is not intended to be a “how-to” but a way to raise the level of awareness of what censorship looks like for those who require unfettered access to information for their work. Using the above diagram, analysts, researchers and everyone else connected to the infosphere can better understand, plan, and develop workarounds to ensure they are receiving the most relevant, accurate, and timely information available, despite the current environment in which we now find ourselves.
Just as censorship is persistent, so are communications. We can expect the map of media and social media sites that we’ve so heavily relied upon for years to look drastically different in a few months compared with what that map looked like just last year.
Censorship is a dangerous and risky tactic. Yet it is one of the most common forms of controlling an individual, group or population. In totalitarian societies, censorship is most commonly practiced by government or through government owned and or controlled businesses.
In Western democracies, as we’ve seen, censorship has increasingly become the preferred method of the media and tech providers themselves. As I have written in the past, it’s not Big Brother that Western society needs to worry about, it’s the 1,000 Little Brothers who are busy fulfilling Orwell’s prophetic warning by proxy.
In a follow-up article, I will discuss methods for analysts and researchers to more effectively evaluate their sources of information in an environment of censorship and ongoing information warfare.

Comments are closed.