By Erik Kleinsmith, Staff, Intelligence Studies, American Military University
Less than a year before his death in 1950, Eric Blair, under the pen name George Orwell, published “Nineteen Eighty-Four,” a dystopian novel about government tyranny by intrusion, surveillance, and manipulation of thought. For Baby Boomers and my fellow Generation Xers, Orwell’s book was often required reading in high school as a warning against the loss of privacy and control in our personal lives.
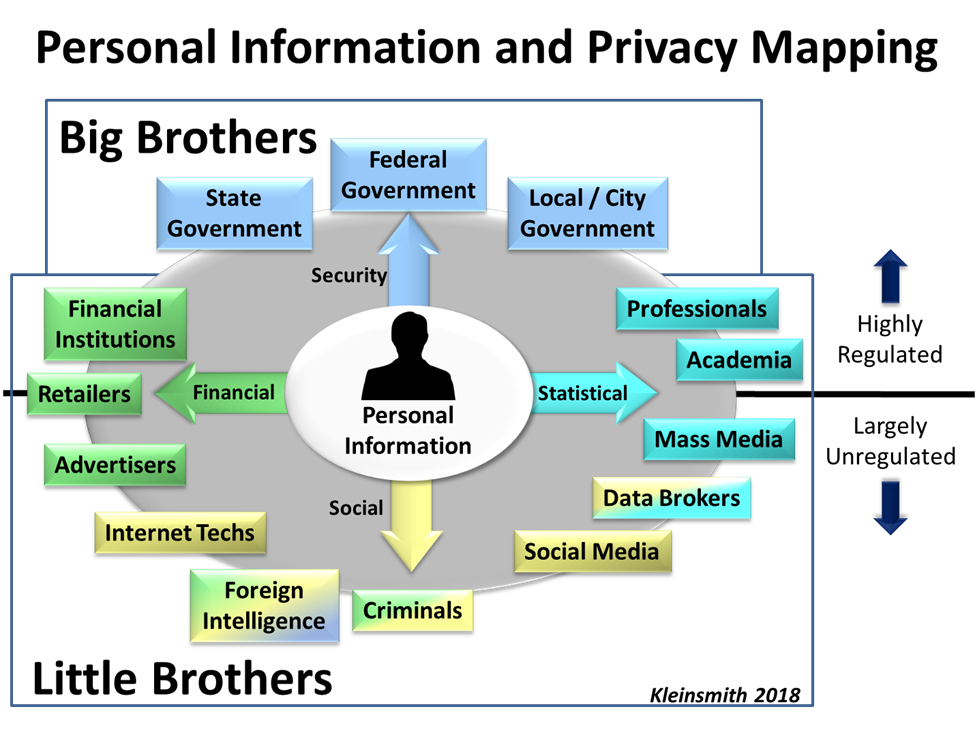
More than 30 years after the title’s year, we’re coming to the realization that it’s not Big Brother that we need to be concerned about as much as Little Brother. The Little Brother effect is largely carried out by non-governmental entities and citizens that are able to collect, process, store, analyze, steal, corrupt, fake and sell information related to almost every aspect of our lives.
More and more, the news is filled with stories about how personal information is being used to benefit others. From revelations after Mark Zuckerberg’s pseudo mea culpa in front of Congress in April, to stories about fake news, identity theft, and how data mining is being used by political campaigns to understand the demographics and psychographics of potential voters, these Little Brothers are collecting massive amounts of personal data—all with our tacit consent.
While it is critical for intelligence analysts, investigators, researchers, and anyone else who relies on publicly available information to evaluate sources of information, it is also critical for the average citizen to look at the where, how, and why their personal information is being collected and used. Mapping out where Big Brothers and Little Brothers are accessing information provides insight into the underlying factors driving today’s privacy concerns.
As this map shows, personal information can be used by many different entities and for many different purposes. The majority of information people share about themselves is required in exchange for access to goods and services.
Sharing personal information with the top half of the map (government entities, educational organizations and financial institutions) is generally deemed acceptable as long as there is confidence that information is protected. Federal laws such as HIPAA for medical privacy, FERPA for educational privacy, and regulations such as Executive Order 12333 for intelligence oversight, are all federally codified protections that ensure trust.
However, these protections are far from perfect. In my own experience working in a military program called Able Danger, I saw firsthand how oversight rules protecting U.S. persons were followed to such a strict degree that we failed to identify and possibly thwart the men who would become the 9/11 hijackers. Nevertheless, for the most part, federal protections provide confidence and security.
Be Leery About Little Brother
While concerns about how Big Brother monitors our communications and activities will never go away, greater privacy concerns should center on Little Brother, as highlighted in the lower half of the chart. There must be public skepticism about how Facebook, Google, Amazon, Cambridge Analytica, and similar companies handle personal information. It is now readily apparent that these companies have the ability to track what we say and do, sell our information to third parties, target us for specific advertising, and change what we see and read. For example, they have the discretion to determine if information is “unsafe to the community,” as in the recent case involving Facebook bloggers Diamond and Silk.
For many of these businesses, personal information has become their currency and a few have been so successful in using this currency that they’ve become veritable monopolies. To better protect private information, there has been recent talk of enhancing regulations on Facebook and other giant tech companies. However, this can be a double-edged sword if proposed changes also prohibit market-based competition. While it is possible for competition and regulations to effect some sort of change, any true solution will only be inflicted if something affects the source of their currency, such as change in the demands of individual users and consumers.
While it’s next to impossible to know the true risks of sharing personal information, people must have a better understanding of where their information goes, who has access to it, and how it’s being used. More so than ever before, people must understand that everything they enter online and every button they click, Big Brother, and perhaps more frighteningly, Little Brother, will always be watching.


Comments are closed.