By Edward J. Hawkins, II
Contributor, InCyberDefense
When you take into consideration our interconnected lifestyles today, we must consider how to balance security, privacy and functionality when we utilize Internet-based resources. While some of the original designers of the Transmission Control Protocol/Internet Protocol (TCP/IP) suite intended for security to be included, it was ultimately left out of the design.
As a result, there is an industry of bolt-on security solutions that may or may not work as intended. Also, there are plenty of profiteers looking to steal your information by selling you fake software that does anything but protect your information.
If you have been using the Internet for a while, you may remember things like dial-up connections, the Integrated Services Digital Network (ISDN), cable or a Digital Subscriber Line (DSL). All of these technologies but the dial-up connection was considered an “always on” connection. Consequently, those systems were vulnerable to unauthorized access from attackers, whereas a dial-up connection required the computer to place an actual phone call.
Today, the Internet is accessible to anyone with a cellular phone, which is a security concern of its own. One of the most endearing things about us humans is our desire to assist our fellow humans; unfortunately, there are criminals that use this good nature against others for their own personal gain.
This practice is known as social engineering, which is a typical topic covered by IT security professionals in cybersecurity training sessions. Social engineering is a major threat to anyone who uses the Internet on a regular basis, because it is designed to leverage our desire to help others or meet some other self-fulfilling need.
Phishing E-mails and Social Engineering
Depending on your experience with the Internet, social engineering takes many forms. The most common form of this threat is a phishing e-mail that you receive in your inbox or junk mail/spam folder. These e-mails will have some subject that is designed to catch your eye or appear to be from someone you know.
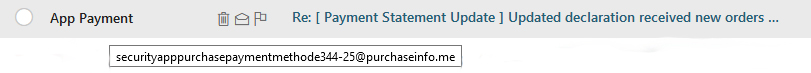
Here is a sample image.
Figure 1. A social engineering attempt using a phishing attack.
This form of social engineering is referred to as phishing. In this type of scam, the attacker sends out a massive amount of e-mails to random e-mail addresses in the hopes that the recipients are not aware of the true nature of the e-mail. In this example, notice that the “Re:” is supposed to be in response to some e-mail conversation that the recipient had started, but in most cases, the recipient never started a conversation.
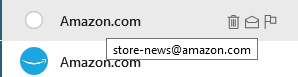
If this were a legitimate e-mail, the “Re:” would not be there and it would be from someone that you recognize, not something generic like “App Payment.” Also, the domain (in this case, purchaseinfo.me) would be from a website that you use on a regular basis, such as Amazon.com or iTunes.com.
An example of this can be seen below:
Figure 2. An example of what you should be looking for.
If you do not recognize the source of communication, do not click on it, but hover your cursor over it and see what happens. If the e-mail looks like it is from someone you know, but the subject looks out of place, call that person to verify that he or she sent you an e-mail.
Social Engineering Scams May Involve Phone Surveys, ‘Click Bait’ Social Media and Fake Websites
While phishing may be one of the most prevalent forms of social engineering in use today, it is not the only type of social engineering scam. Other forms of this security threat are unsolicited phone calls doing surveys or other forms of data gathering, click-bait found on social media platforms, and websites with URLs that have been created to look like a legitimate version of a business webpage.
An example of this can be seen in the following example: AOL.com verses A0L.com. To the untrained eye, it may appear that the two web addresses are the same, but the latter version uses a zero in a different font. It is these slight differences that could result in going to a website that you want or going to a fake, malicious website that the threat actor wants you to visit.
Social Media Platforms Also Present Social Engineering Hazards
Social media platforms are good and bad, depending upon your perspective and understanding. I see them as a necessary evil in today’s interconnected world.
Take, for example, this news article from 2012 that discusses how Chinese spies used fake Facebook profile to friend NATO officials. While you may think, “This will never happen to me; I am not that important,” bear in mind that someone may try to use your connection to someone else purely due to your association with that other person.
My rule of thumb for social media: create a social media account with a picture of you in your profile and only “friend” those people that you personally know or can validate. This practice allows you to set up e-mail alerts and helps your friends to identify threat actors who may be trying to use your image for their own personal gain.

Comments are closed.